
Cyber security is one of the biggest and most prominent concerns in contemporary business. The vast cost of falling prey to phishing, ransomware or some form of social engineering based attack, is both punishing and a highly concerning backdrop to any commercial organisation carrying out its business activities.
Cyber threat actors have grown and diversified.
In the UNICC (United Nations International Computing Centre) Cyber Threat Landscape Report 2022, based on the intelligence gathered and the attacks analysed by its teams, four cyberthreat categories were defined and categorised - based on their respective goals.
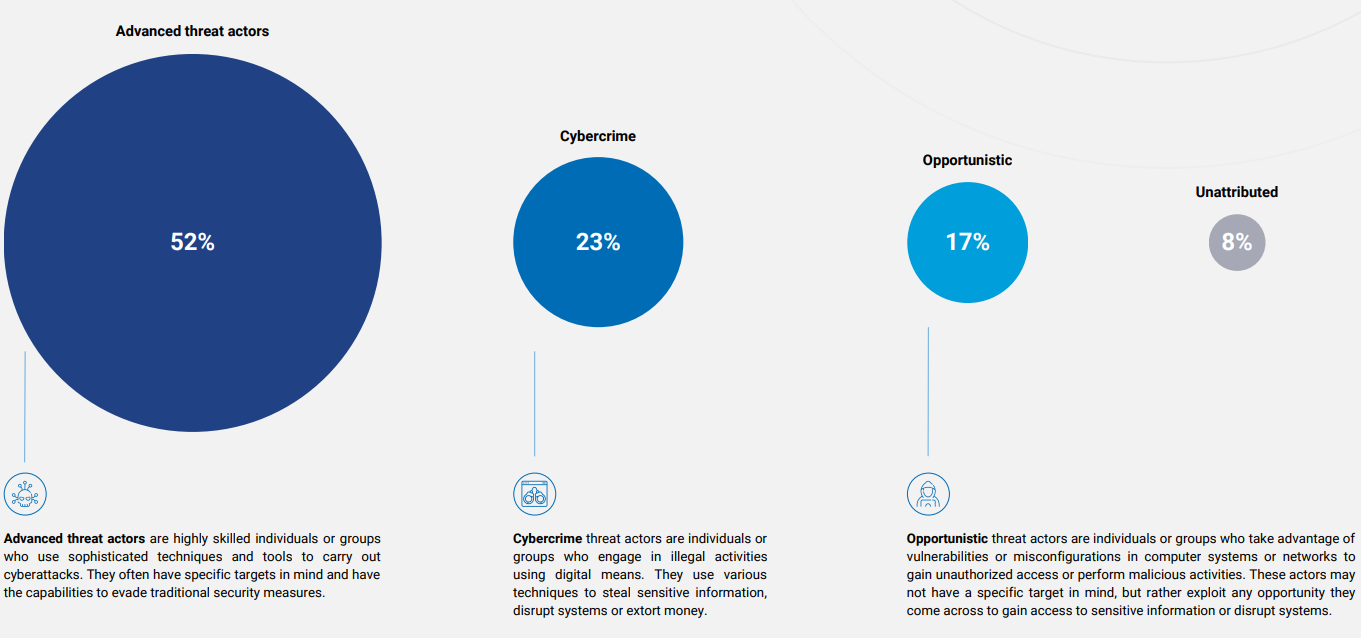
While the report includes emphasis on the threats and vulnerabilities around Governmental and Political targeting, the infographic does provide a snapshot into the types of attacks and what groups and threat actors are responsible for them.
The report states that Advanced Threat Actors use sophisticated techniques and tools to carry out cyber attacks, including ransomware, malware, zero-day exploits and denial of service attacks. Cybercriminals are also likely to use and leverage many of these techniques as they are highly lucrative and proven to yield big payouts, which is usually the intention.
In a recent survey by Sophos, ransomware payments have almost doubled between 2022 and 2023, with more than a quarter of those surveyed having paid out between $1-5million to restore access to their locked, stolen or encrypted data.
This theme of accessing and stealing valid and operational data and more importantly, credentials is further enabled by the explosion of demand and availability of such details in dark web or black marketplaces. Known as broker access services, there is a lucrative and high demand market for exploited, stolen and revealed access details for various cloud services. This has in recent years moved the exploit styles away from the need for malware and viral payloads as essentially there are simpler and more efficient ways to gain access to cloud based services and infrastructure.
Malware is old-school when someone leaves the door open.
In the CrowdStrike 2023 GLOBAL THREAT REPORT, it was reported that 71% of reported attacks were malware free, relying instead on hands-on methods with available access credentials.
Anyone that has had a cloud service hacked (such as a social network) will know that once in, they have full control to be able to infiltrate other connected users accounts acting as "you."
To exacerbate things further social engineering vulnerabilities are present where one set of access credentials can often be "daisy-chained. " In the pursuit of convenience and not having to remember or store multiple passwords, users can repeat use of a favourite or known-to-them password which on reflection, offers a clear and simple path to one exploited account spiralling into access of many systems.
In such cases, hacking of a non-critical app like a book membership or fitness app may not create major disturbance to life, but if the credential used (usually formed as an email account as username and a selected password) is used in many networks, then suddenly it can access and reveal more sensitive information such as those details that would allow a threat actor to access details that would enable bypassing of financial security checks (DOB, first line of address, etc)
Why does it matter so much to Sugar Rush?
It is these kinds of easily patched vulnerabilities and reshaping of how we think about access to systems and protecting our information, that has led to Sugar Rush taking a lead on behalf of our clients. Our aims were simple.
To take a deep dive into the vulnerabilities that are present/potentially present around our dealings with clients and their projects
To commit to a security conscious mindset in all of our commercial and non-commercial activities.
To provide a leadership and advice to our clients and prospective clients on how to take preventative steps around protection of all privileged data.
We have placed higher focus on the concept of privileged data rather than "sensitive" data as all data belonging to or accessed under privilege must be protected with all reasonable steps to avoid any further resultant vulnerabilities from one system to the next.
The entire team went through a rigorous program of training to raise our corporate awareness of cyber security considerations and pinpoint vulnerabilities and actions needed respective to our individual roles. We worked with Cyber Security Auditing experts who undertook a painstaking and detailed look at our business processes and data protection methodologies and indeed our own preconceived ideas around the protection of privileged data both in and outside of the workplace.
The result was a set of clear and cohesive standards to act as a foundation for all of our client facing and back-office business processes including the deployment of some specific tools and strategies adherent to these important standards.
Our ISO27001 is a badge of honour (but the big work starts now)
We've earned it and it's important to Sugar Rush as an achievement. It is however also a statement of commitment - to the security and proper treatment of the data our clients entrust to us.
We are proud of what we've achieved but highly cognisant that in an ever-evolving cyber threat landscape where there is a critical need for leadership and guidance -the big work starts right here and right now.







